Product Security FAQ
Frequently asked questions about the Product Security IoT Device Security Specification and its Certification Program.

What is the purpose of the Product Security Working Group?
The purpose of the Product Security Working Group is to develop a product security certification program informed by security best practices, technical capabilities, and existing product security regulations used to assure the security of IoT devices and ultimately grant a mark recognized by consumers that the products they are using satisfy a baseline security threshold and can be endorsed by regulators as satisfying applicable security requirements. Authorized Test Labs are employed to deliver this mark at scale.
What is product security and how does it differ from protocol security?
Standards such as Zigbee and Matter define requirements for the security of network protocols. The Product Security Working Group supplements these by creating a certification program for the security of products as a whole, including security features such as secure boot that are inherent in the product but not part of a network protocol. Additionally, this program is available to products that do not implement any protocols standardized by the Alliance.
Why do we need the Product Security Working Group when the other Alliance technologies already have security requirements for their certifications?
Product security certification differs substantially from the functional and interoperability testing employed by our other working groups. With product security, testers must verify not only that a product properly functions and interoperates but also that it can resist certain hostile attacks. Thus, product security certification requires different skills and methods.
For example, a product with a well-known admin password or backdoor might pass functional and interoperability tests but not product security tests.
Why does the Alliance need to create a product security certification?
Attacks against IoT systems continue to grow, in numbers, sophistication, and impact. Those attacks exploit any possible vulnerability beyond the traditional scope of connectivity protocols, which are typically restricted to securing commissioning and data in transit.
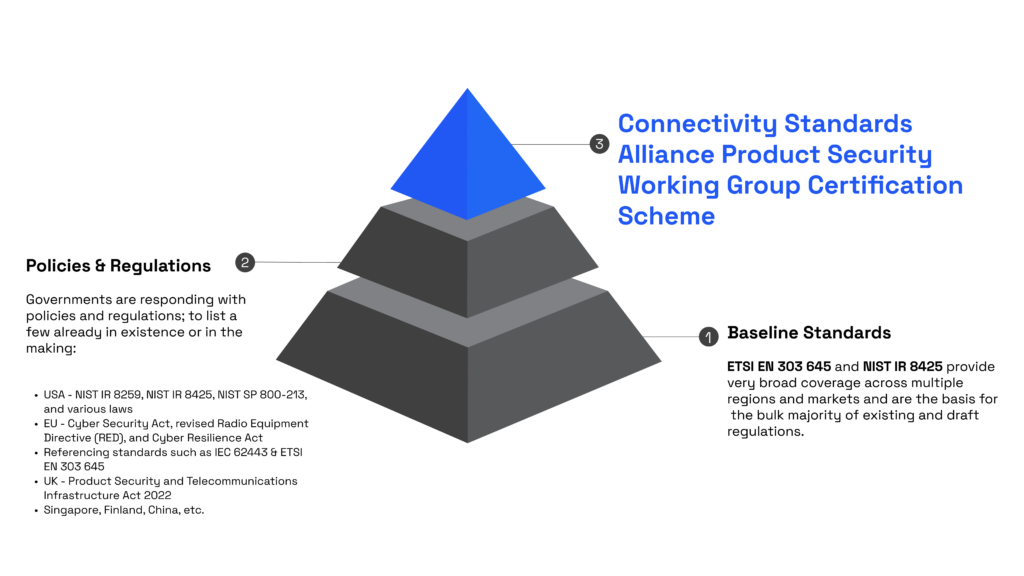
National cyber security certification/labeling programs are starting to emerge (e.g. Singapore and Finland) and governments are responding with standards and regulations; to list a few already in existence or in the making:
- USA – NIST IR 8259, NIST IR 8425, NIST SP 800-213, and various laws
- EU – Cyber Security Act, revised Radio Equipment Directive (RED), and Cyber Resilience Act
- Referencing standards such as IEC 62443 & ETSI EN 303 645
- UK – Product Security and Telecommunications Infrastructure Act 2022
- Singapore, Finland, China, etc.
Continuing divergence of requirements and proliferation of different certification programs will lead to high costs and complexity of proving product security before market placement, especially for global players.
The Alliance’s ambition is to remedy this situation by leveraging its strengths and expertise: providing a market-valued certification program developed in a consensus-driven standardization process, informed by security best practices, technical capabilities, and existing product security regulations.
How does the Connectivity Standards Alliance Product Security certification relate to national, regional, and international standards in this area?
The Product Security certification is based on the requirements included in national, regional, and international standards related to IoT product security. We expect that products that receive the Alliance Product Security certification will also comply with these other standards, simplifying the certification process for product manufacturers and consumers alike.
How many Alliance member companies are involved in the Product Security Working Group?
At the time of the Product Security 1.0 IoT Device Security Specification release, there were nearly 200 Connectivity Standards Alliance Promoter and Participant member companies represented in the Product Security Working Group.
What are the security features and requirements that are included in the specification and that must be certified by the Alliance? What does a secure product under this mark stand for or entail?
The Product Security’s IoT Device Security Specification includes dozens of specific product security provisions. IoT Device Manufacturers must attest their compliance with those provisions, supplying justifications and evidence to a certified Accepted Test Laboratory with expertise in security evaluation and experience certifying products relative to this specification.
- Specific requirements include
- Unique identity for each IoT Device
- No hardcoded default passwords
- Secure storage of sensitive data on the Device
- Secure communications of security-relevant information
- Secure software updates throughout support period
- Secure development process, including vulnerability management
- Public documentation regarding security, including support period
Together, these requirements provide assurance that fundamental security requirements have been met.
If certified, is the Verified Mark for Product Security required to be on the device or packaging?
No, the Verified Mark will be optional for Device Manufacturers to put on the device or packaging. They can go through the certification program and claim certification without showcasing the mark.
